Our managed security services give your organization access to best in class experts, proven processes, and cutting edge technologies that fit your requirements and budget.
68%
of business leaders felt the risk of a cyberattack increasing.
68.5%
percent of businesses were victimized by ransomware
59%
of SMBs go under 6 months following a cyber attack.
What is Penetration Testing ?
Penetration Testing can consist of a variety of activities designed to simulate real-world attack scenarios against a business’ IT and physical security controls.
The ultimate goal of a penetration test is to validate the vulnerabilities identified during the scanning phase, and investigate any other avenues of penetration through reconnaissance.
Why are pen tests performed?
Knowing about vulnerabilities is just one step toward a secure enterprise. Penetration testing is conducted to validate not only the vulnerabilities already identified, but to evaluate the implementation of security controls and tools.As sophisticated as security device are today, almost 90% of cyber attacks are caused by human error or behavior. Security misconfiguration can happen at any level of an application stack, and these are the targets of modern hackers.
Modern attackers face sophisticated security controls and smaller attack surfaces, which has caused a shift in the approach to attacking an enterprise.
Straightforward attacks have evolved into elaborate campaigns of reconnaissance, data collection, phishing, fraud, theft, and social engineering to circumvent these advanced tools.
90% of cyber attacks are caused by human error or behavior
Our penetration testing services
Protect your business from advanced cyber attacks
White Box & Black Box Testing
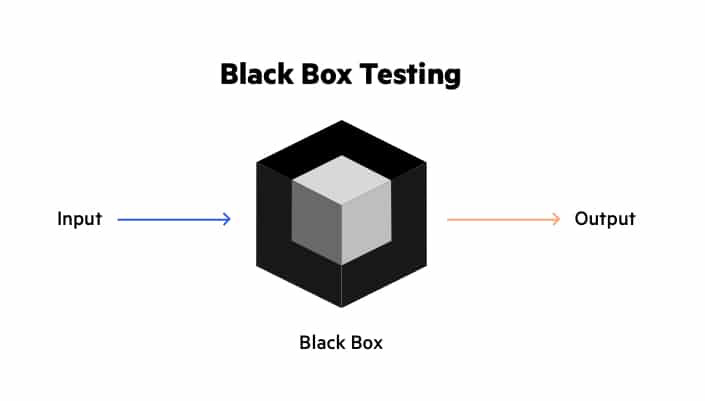

White Box & Black Box Testing
Network Testing
Web Application Testing

Web Application Testing

Wireless Testing
Social Engineering Testing


Social Engineering Testing
Physical Testing
Project deliverables
Our Strategic Partners & Vendors







How It Works With PDG IT Solutions

We begin every engagement with a friendly chat to better understand your company’s cyber security goals.

A security engineer will be assigned to retrieve asset information and connect the hosts through a secure tunnel.

Extensive application and network penetration testing conducted. Analysts assigned as emergency stand-by and support.

Observations and recommendations collected and formatted into an executive report – including steps towards remediation.

We begin every engagement with a friendly chat to better understand your company’s cyber security goals.

A security engineer will be assigned to retrieve asset information and connect the hosts through a secure tunnel.

Extensive application and network penetration testing conducted. Analysts assigned as emergency stand-by and support.

Observations and recommendations collected and formatted into an executive report – including steps towards remediation.
